Fight Crime with Kafka Streams and the Bintray Firehose API
A presentation at Oracle Code One 2018 in in San Francisco, CA, USA by Viktor Gamov
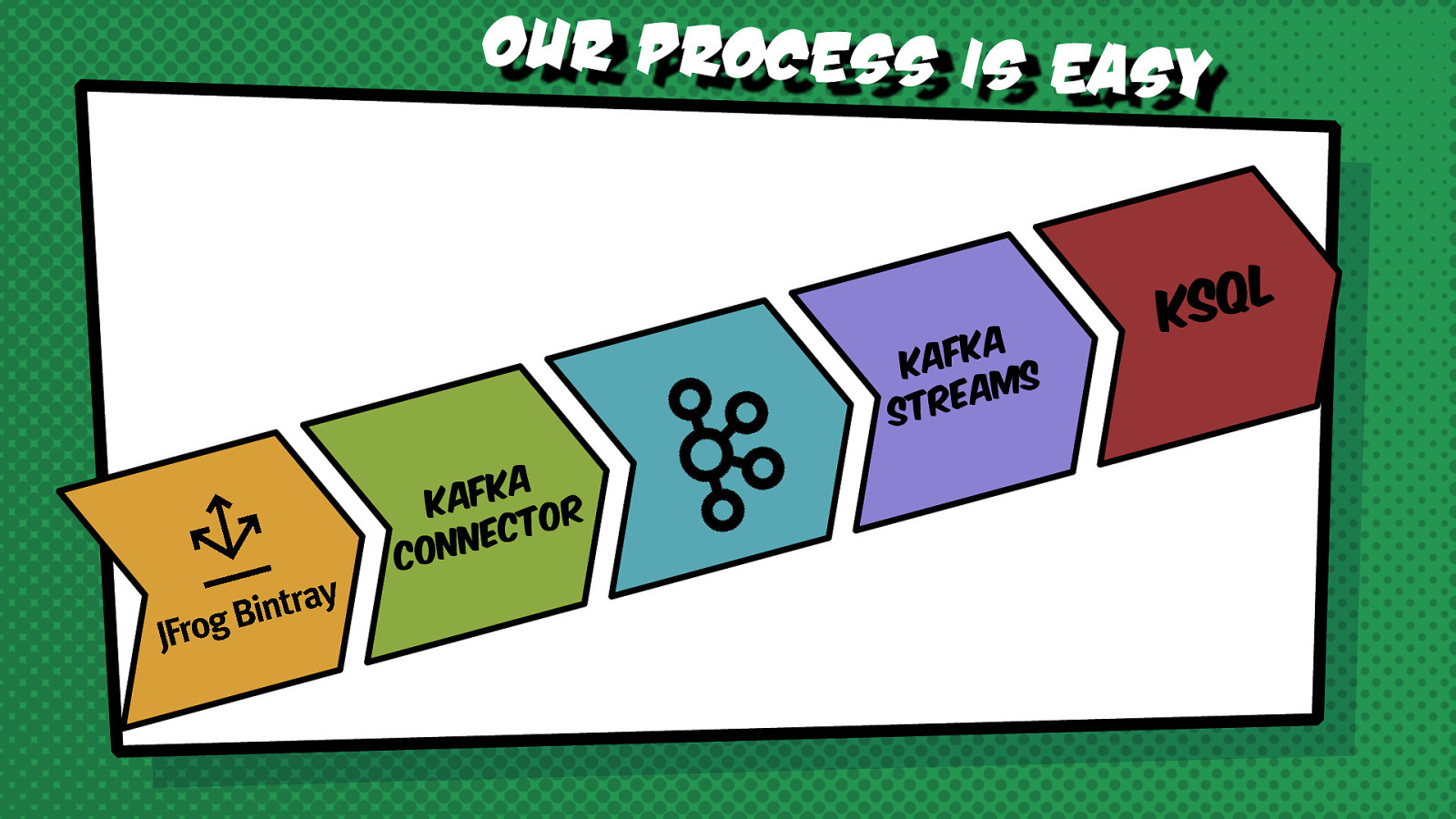
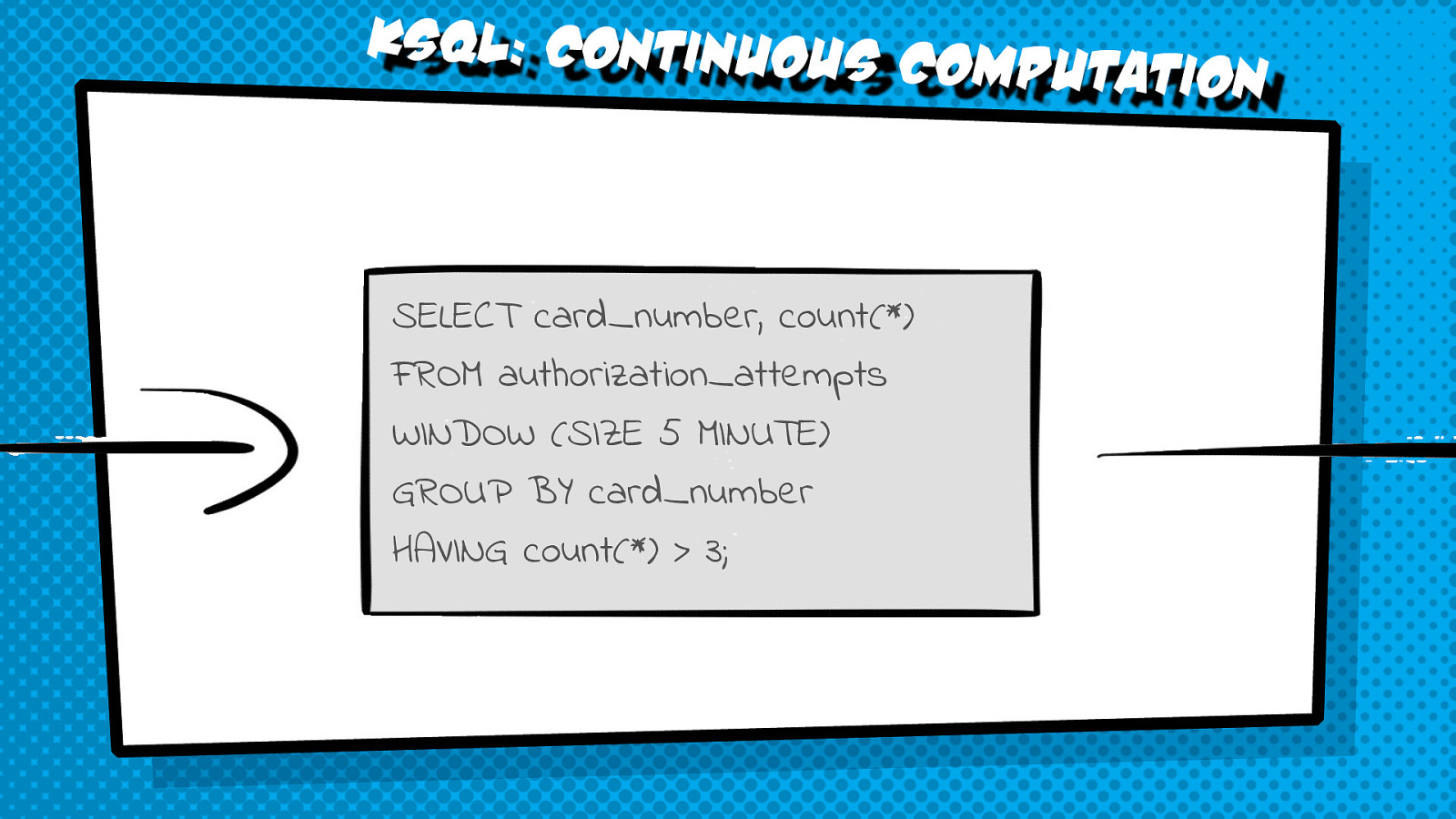
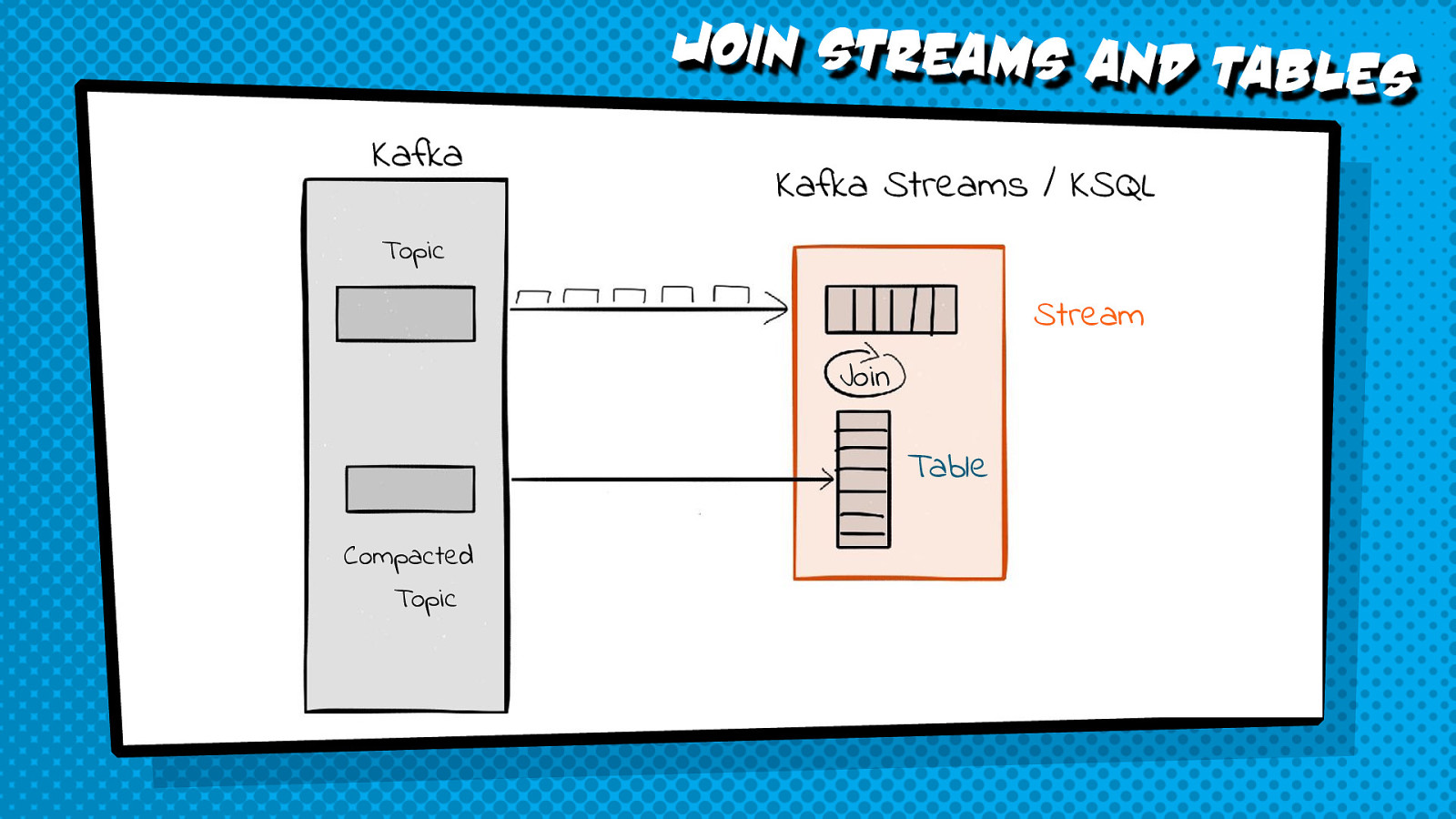
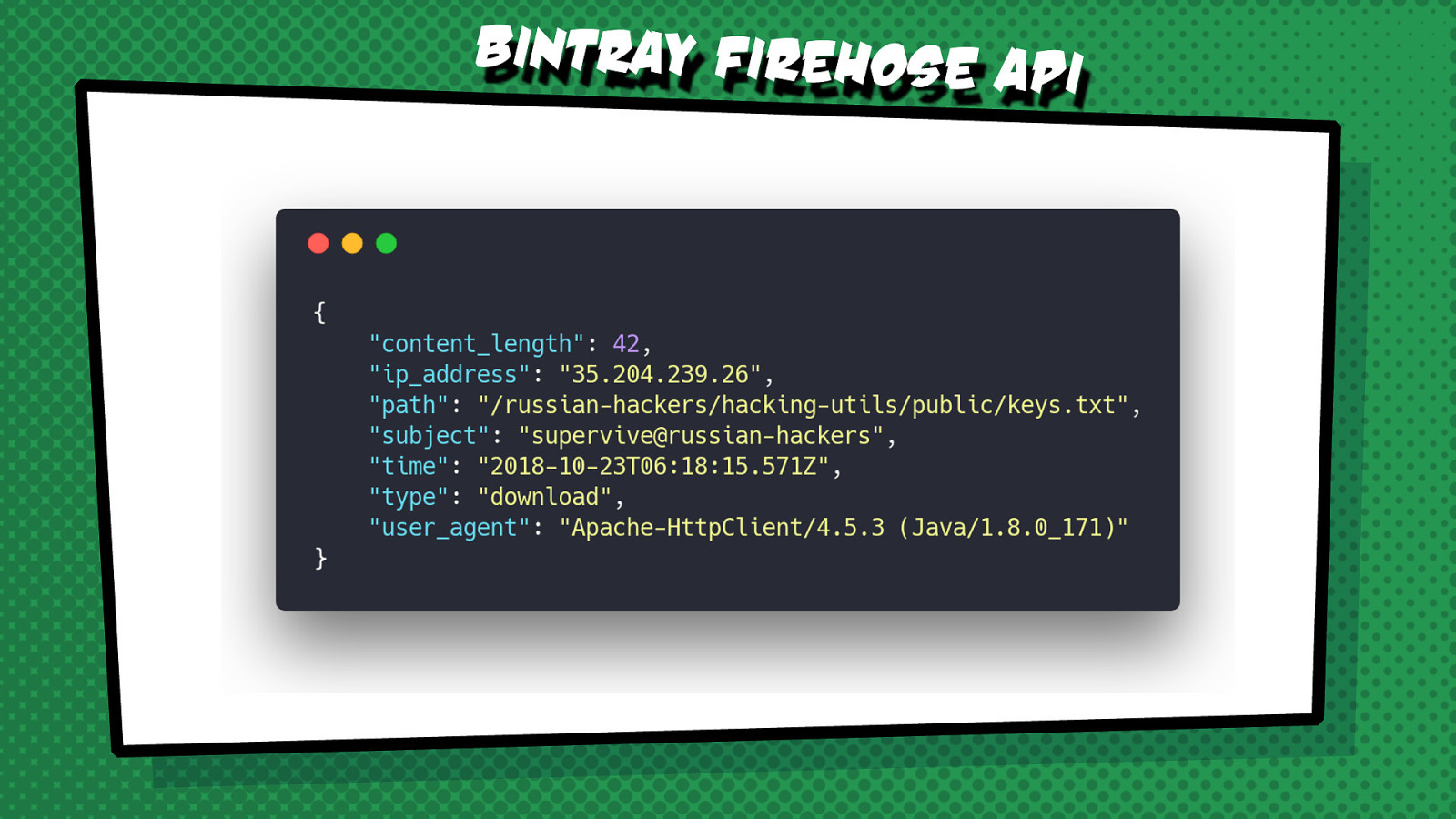
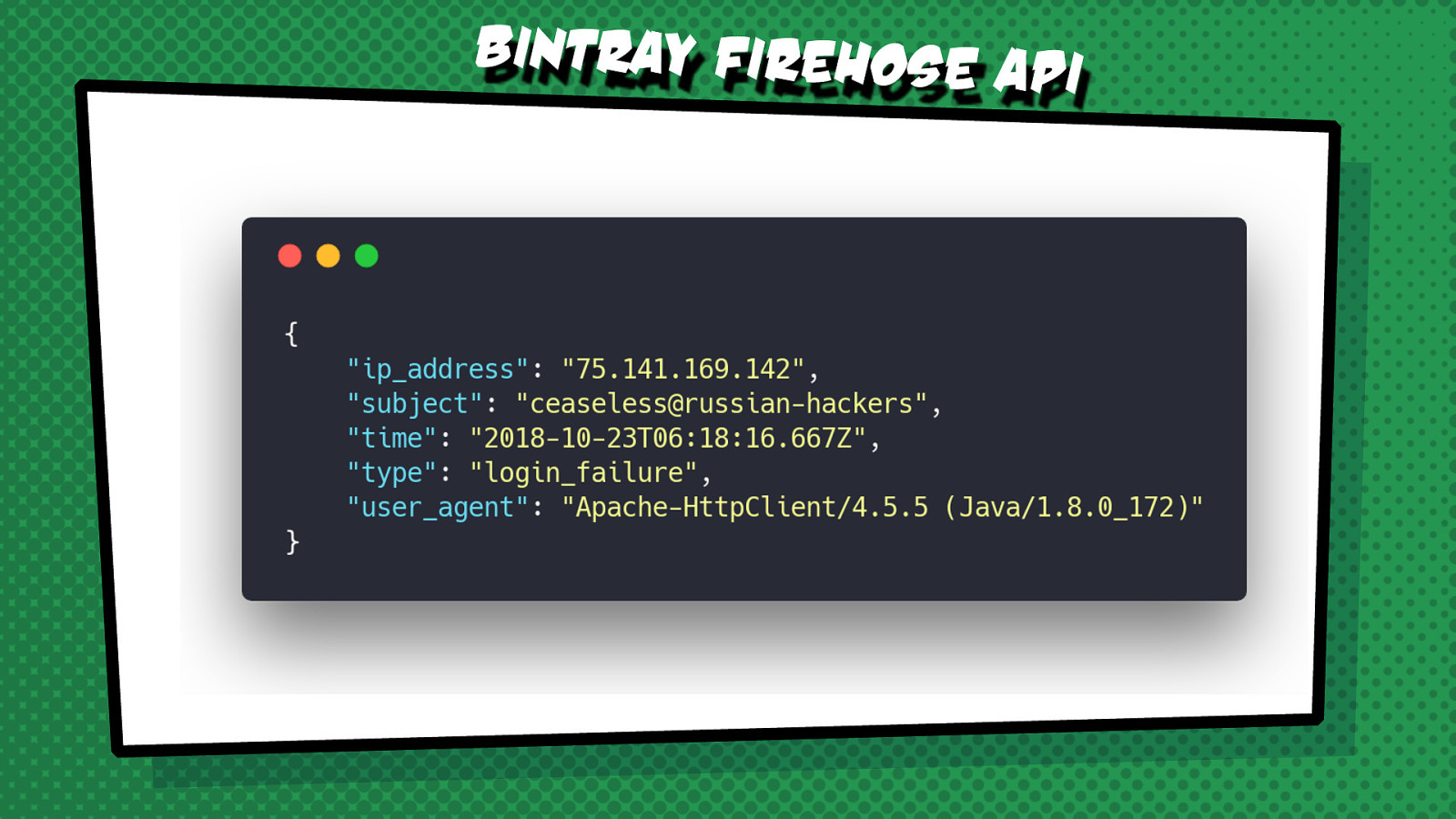
Can you find a malicious activity needle in the haystack of events on one of the busiest distribution hubs in the world? Processing the streaming events from the Bintray Firehose API with Kafka Streams can give you the superpower to do that. This session shows a real-life example of using Kafka KSQL to process and parse huge amounts of data to identify a worrying trend that might be a sign of a malicious activity.
Code
The following code examples from the presentation can be tried out live.